WordPress is known to be one of the most used online applications, as such hackers are specifically targeting it for their own malicious intents like spreading SPAM or getting hold of personal information. Here, we’ll check how you can clean an infected application and implement further security for your WordPress installation.
Making sure your machine is clean
It is important that you have secured your own personal machine before you consider taking care of your online security as well. You can use an Anti-Virus Program to scan your computer and keep it clean of any Malware
Scanning your hosting account
Perform regular scans of your hosting account! On any Shared Packages you can do that through your cPanel account:
cPanel -> Virus Scanner -> Scan Entire Home Directory -> Scan Now
Cleaning infected files
Go through the logs that the Virus Scanner made if any infected files are found you should review each of them and see how they interact with your Applications and Installations, then clean them of any malicious content. For example, most exploited files contain random strings (often known as obfuscated code) that are used to distribute SPAM from your account. For example, an exploited file might look like:
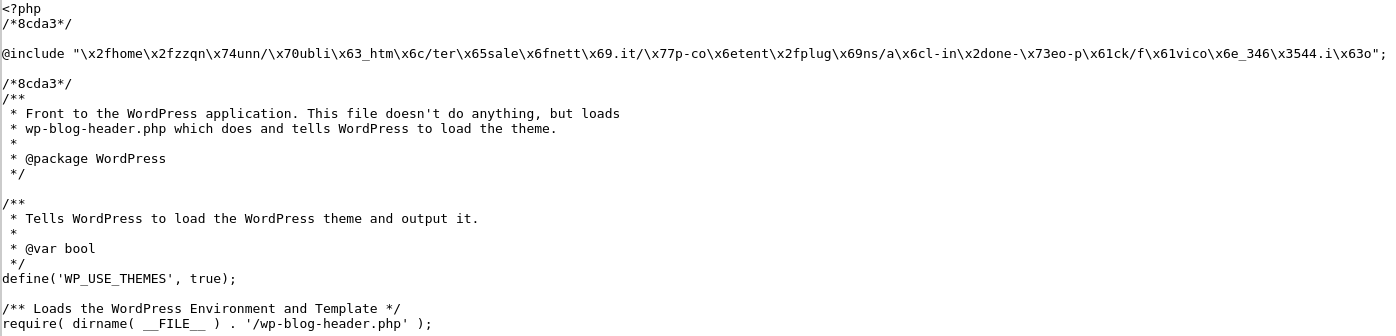
You can see several lines at the top like @include and many random strings afterwards. This loads additional malicious code that is executed every time your website is loaded – it should be removed, in the example above the new index should become like:
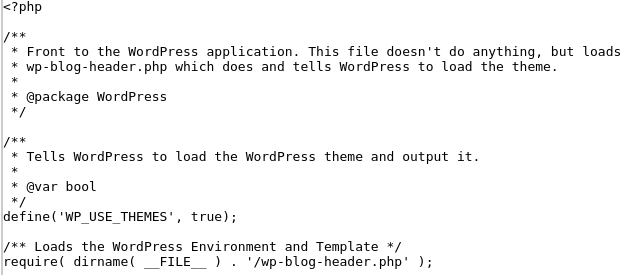
Other files could have legitimate names like index.php but be placed in totally non-relevant directories like
/home/cPanelUsername/domainRootDirectory/wp-Something/index.php
The legitimate folders present in a Standard WordPress Installation Root Directory are: wp-admin, wp-content, wp-includes, other directories could be present due to the exploitation of your account. You should make sure that the directories are not needed before you delete them, in the example above a such file contained:
![]()
It is safe to delete that file as it contains only malicious code. And the directory also, as it contained only exploited files. Before cleaning any files you can also take a look at WordPress’s official GitHub page at https://github.com/WordPress/WordPress to see what they look like by default. Keep in mind that some files like wp-config.php contain custom settings specific just for your own installation.
Changing Passwords
You should consider changing the passwords of your hosting account after all the files that were marked malicious by the Virus Scanner tool are cleaned. Those passwords involve the following services:
- Your cPanel account’s password
- The password of each email that you have hosted in your cPanel account
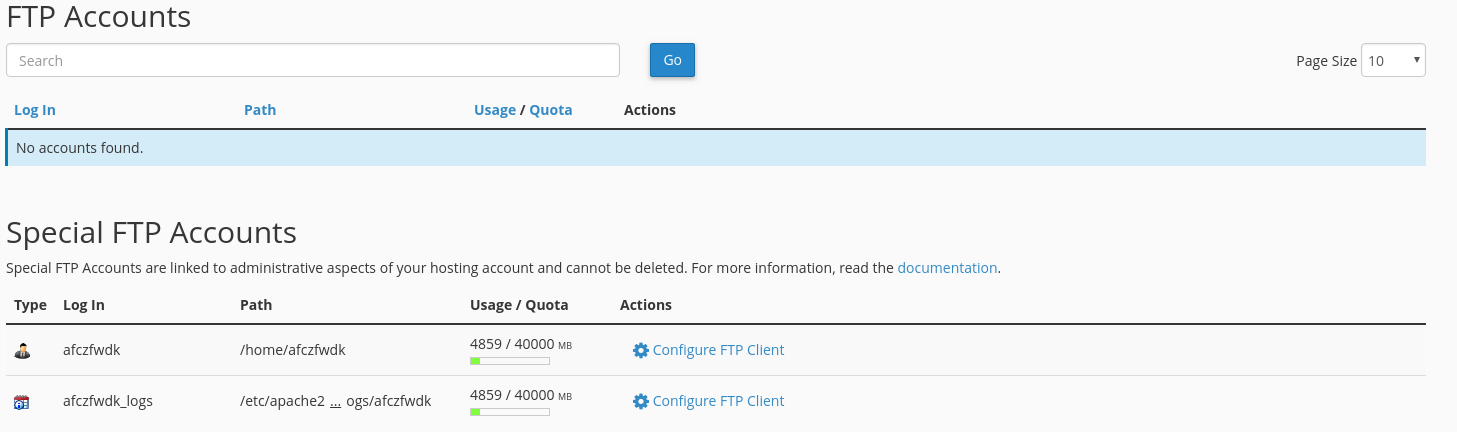
- Your FTP account’s passwords. It is also important to make sure that there are no additional FTP accounts present in your cPanel. If you haven’t made any FTP accounts your cPanel -> FTP Accounts tool should show just cPanel username and cPanelUsername_logs as FTP accounts:
Fixing files and folders’ permissions
In most cases, the files and folders of your cPanel account should be fixed – 644 for files and 755 for folders. Those permissions can be changed by hackers to ease further exploits against your account and should be verified. One of a few exceptions is custom PHP logging libraries that also require RWX permissions for folders that they will write into, Magento installations use such for example. Apart from manually adjusting permissions, you can also do that through SSH:
1. Log in to your account via SSH (you can look up our guide here)
2. Run the following commands (know that this will make all files’ permissions 644 and folders’ 755)
find . -type d -exec chmod 0755 {} \; # makes all folder permissions 755
find . -type f -exec chmod 0644 {} \; # makes all files permissions 644
Making sure Database hasn’t been exploited and no Backdoors are present
It is common that in addition to files that the Database of an exploited application is also exploited. In most cases, hackers add their own User and make them have Administrator Privileges, this way they have full access not only to your hosting account’s files but to your website and any personal information on it as well. For WordPress applications, the Database Table is called wpDatabasePrefix_users and their metadata is stored in a table wpDatabasePrefix_usermeta. Those entries need to be removed as fast as possible
Navigate to your Database via phpMyAdmin (cPanel -> phpMyAdmin)
Locate the Database that’s in use for your WordPress installation
Locate the wpDatabasePrefix_users Table. The Column called `user_login` is the one corresponding to any registered user that you have on your website. Any user that you do not recognize should be deleted, the process involves several steps, however. Lookup for any unrecognized users and remember their `ID`. Click Delete afterwards
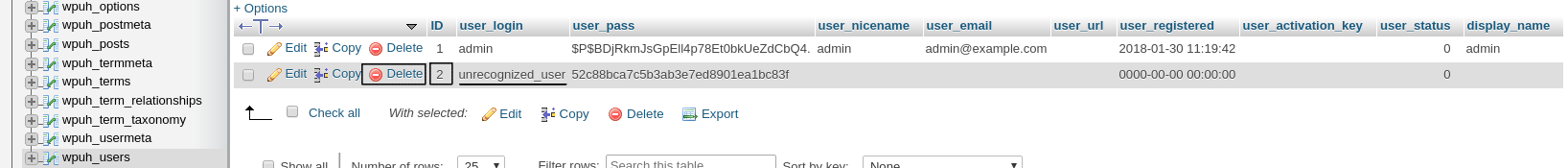
Navigate to the table called wpDatabasePrefix_usermeta. Here we should sort by `user_id` and find all entries that contain the `ID` from the wpDatabasePrefix_users table, then they should be deleted

Alternatively those entries can also be deleted by executing the following command through phpMyAdmin -> SQL (on the top)
DELETE FROM `wpDatabasePrefix_usermeta` WHERE `user_id` = 'UNRECOGNIZED_USER_ID';
Note:
There you should change the wpDatabasePrefix and UNRECOGNIZED_USER_ID with the ones for your installation, in our case they are:
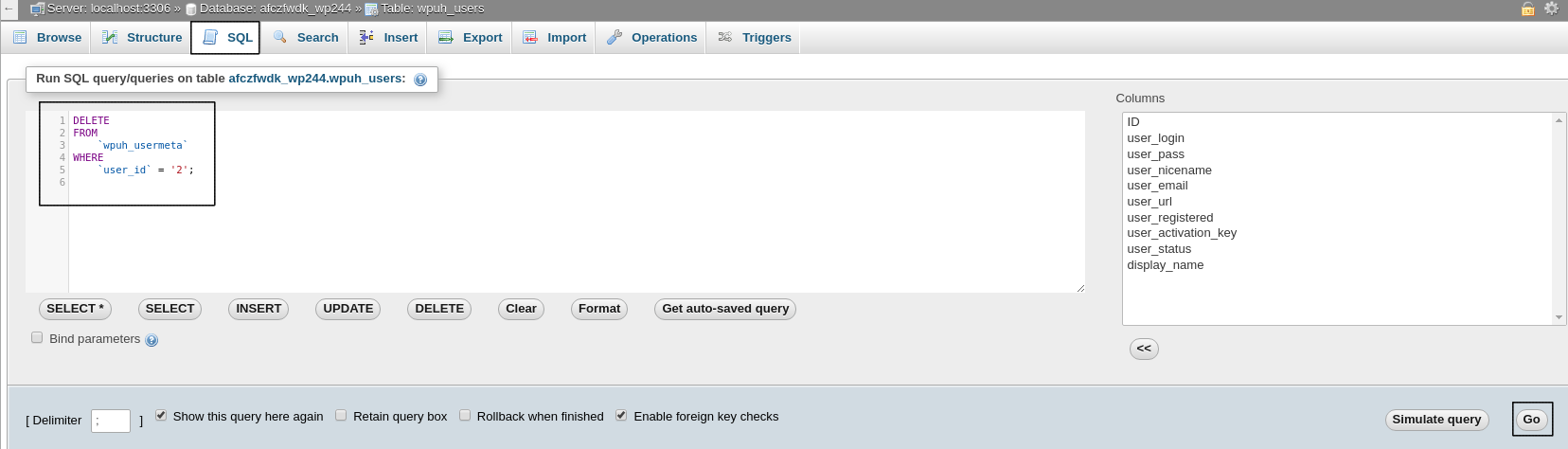
This should assist greatly to clean your hosting account out of exploited files. It’s also recommended to use the Virus Scanner at least once per week to make sure your installations are not infected.
Further security
After this, your hosting account and application should be secure and cleaned up of any malware present in it. This, however, might not prevent future exploits. To guard yourself against further exploitation of your account you should also consider:
- Updating your application to the most recent version
- Updating your application’s Theme
- Updating your application’s Plugins
- Deleting all Themes and Plugins that you’re not using (default Themes should be deleted if not used)
- Installing / Implementing Security Plugins
- Contacting a developer that can assist with security
Note:
Before making any updates or changes you should back up your installation’s files and database!
Cleaning a website requires a lot of work, experience and time. You can always rely on our professional services or Managed Hosting services.



























